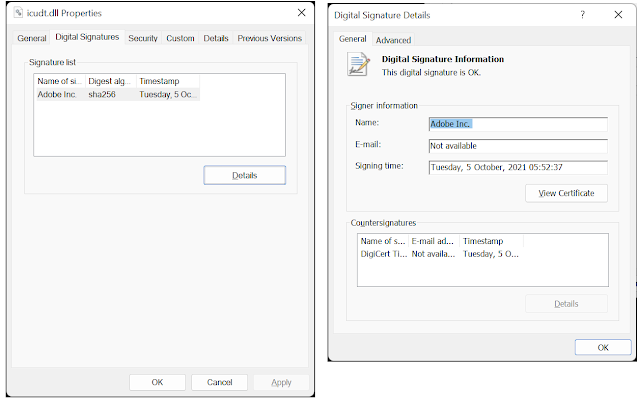
Digital Code signing binaries such as exes, dlls , scripts by the software supplier is now a de facto requirement. The digital signatures not only identifies the source of the software but also asserts authenticity. Also AppLocker rules can be configured to check digital certificates.
Digital Code signing is usually done as part of the build process where binaries are digitally signed as they are built. However this can impose overhead and add complexities in development build environments. Also there could be older digitally unsigned 3rd party binaries supplied as a part of the software. An ideal solution would be to do digital signing as a separate step during nightly production builds as discussed below:
A digital certificate issued by vendors such as Verisign. This is to authenticate the source of the software. It's basically cryptographic public key.
- It is invoked before creating the iso file of the software before deployment.
- It recursively extracts binaries in msi, .zip, cab files, digitally signs them using signtool.exe and packages back.
Extracting and packaging a msi file is done using installer APIs as discussed here.Extracting and packaging a cab files is done using CabArc.Exe.Extracting and packaging a zip files is done using 7z.Exe.

No comments:
Post a Comment